Roles
The Role is a set of permissions to the different sections and actions in Storware Backup & Recovery. When multiple roles are assigned to the Group, the resulting permissions will be the sum of all permissions from all assigned roles.
Note:
It is mandatory to have always at least one account with permission to manage Users
in other words: at least one account must be assigned to the group, which has a role with this permission.
Permissions
Nodes
Instances
Read - allows you to view the list of instances and basic information Register - allows you to register new nodes in the environment
Write - allows you to change selected node config
Delete - allows you to remove a node from the environment
Nodes
Node Configurations
Read - allows you to browse the list of configs and open them
Write - allows you to modify existing configs and create new ones
Virtual Environments
Instances
Read - allows you to browse the list of instances and open them
Write - allows you to modify virtual machine settings
Backup - allows you to perform a manual backup
Restore - allows you to perform a manual restore
Snapshot - allows you to perform a manual snapshot
Mount - allows you to mount a backup for file-level restore
Clean old Snapshot - allows you to perform the "Clean old snapshot" task
Virtual Environments
Infrastructure
Read - allows you to browse the list of infrastructure objects for all tabs
Write - allows you to modify settings for existing objects and to add new ones
Test Connectivity - This permission allows you to enable or disable access to the connectivity test
Virtual Environments
Backup SLAs
Read - allows you to browse the list of policies and schedules
Write - allows you to modify the existing and add new ones
Virtual Environments
Snapshot SLAs
Read - allows you to browse the list of policies and schedules
Write - allows you to modify the existing and add new ones
Virtual Environments
Recovery Plans
Read - allows you to browse the list of policies and schedules
Write - allows you to modify the existing and add new ones
Virtual Environments
Mounted Backups
Read - allows you to browse the list of mounted backups and also to download files
Unmount - allows you to unmount a backup
Applications
Instances
Read - allows you to browse the list of instances and open them
Write - allows you to modify virtual machine settings
Backup - allows you to perform a manual backup
Restore - allows you to perform a manual restore
Applications
Execution Configurations
Read - allows you to browse the list of execution configs
Write - allows you to modify the existing and add new ones
Applications
Backup SLAs
Read - allows you to browse the list of policies and schedules
Write - allows you to modify the existing and add new ones
Storage
Instances
Read - allows you to browse the list of instances and open them
Write - allows you to modify storage instance settings
Backup - allows you to perform a manual backup
Restore - allows you to perform a manual restore
Snapshot - allows you to perform a manual snapshot
Mount - allows you to mount a backup for file-level restore
Clean old Snapshot - allows you to perform the "Clean old snapshot" task
Storage
Infrastructure
Read - allows you to browse the list of infrastructure objects for all tabs
Write - allows you to modify settings for existing objects and to add new ones
Test Connectivity - This permission allows you to enable or disable access to the connectivity test
Storage
Backup SLAs
Read - allows you to browse the list of policies and schedules
Write - allows you to modify the existing and add new ones
Storage
Snapshot SLAs
Read - allows you to browse the list of policies and schedules
Write - allows you to modify the existing and add new ones
Storage
Mounted Backups
Read - allows you to browse the list of mounted backups and also to download files
Unmount - allows you to unmount a backup
Reporting
Reporting
Read - allows you to view report data for virtual machines and storage providers Send report - This permission allows you to enable or disable the ability to send the report by mail
Reporting
Audit Log
Read - This permission allows you to enable or disable access to the audit log report
Backup Destinations
Backup Destination
Read - allows you to browse the list of backup destinations
Write - allows you to modify settings for existing objects and to add new ones
Test Connectivity - This permission allows you to enable or disable access to the connectivity test
Clean old backups - This permission allows you to enable or disable the ability to perform this task
Access Management
Access Management
Read - allows you to browse the list of objects for all access management tabs
Write - allows you to modify existing objects and to add new ones
Change passwords - allows you to change user passwords
Settings
Settings
Read - allows you to view selected settings for all tabs in the "settings" section
Write - allows you to modify settings for all tabs in the "settings" section
Tasks Console
Tasks Console
Read - this permission allows you to hide or show the "Task Console" floating panel
Write - allows you to remove/cancel tasks from the list
Restore Job
Restore Job
Read - This permission allows you to enable or disable access to the information about restore tasks - under tasks console, details of virtual machine or storage instance and from recovery plans
Security contexts
The security context defines the set of system objects that can be accessed with defined permissions.
The object hierarchy is constructed in a way that any defined privileges will apply to the specified object and to all the downstream objects, therefore the System Level security context defines the access to all objects across the platform and disables the choice of lower-level objects.
Security contexts have been aggregated into the specified hierarchy. Different system object types can have different parental objects (or none) and so will appear in the different sections of the tree.
Selected objects will be visible in the table on the right-hand side.
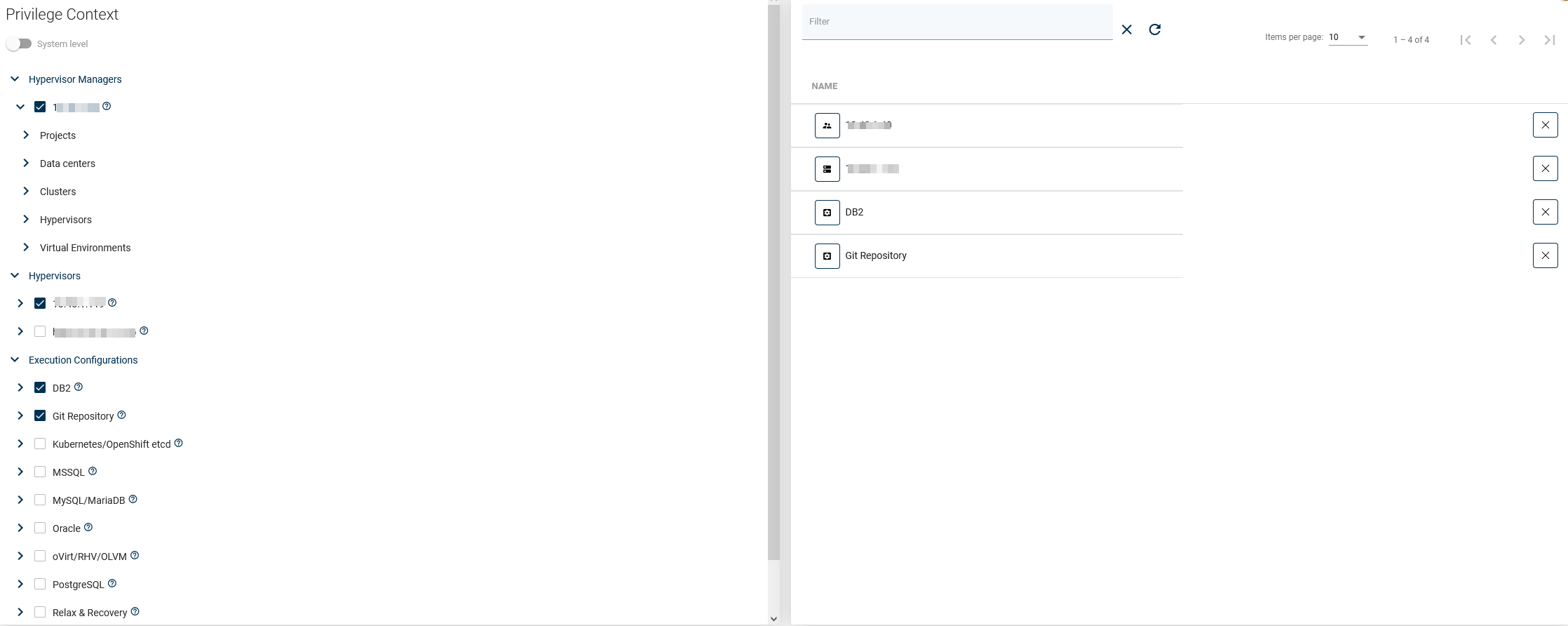
The full hierarchy:
Hypervisor Managers
Projects
Virtual Environments
Data Centers
Hypervisors
Virtual Environments
Clusters
Hypervisors
Virtual Environments
Virtual Environments
Clusters
Hypervisors
Virtual Environments
Hypervisors
Virtual Environments
Virtual Environments
Hypervisors
Virtual Environments
Application Configurations
Applications
Storage Providers
Storages